In this blog post, we’ll walk through the steps to manually trust the Machine SSL certificate and recognize it as valid on a Windows machine when accessing vCenter. This way, you won’t have to validate the certificate every time you access the vCenter Server.
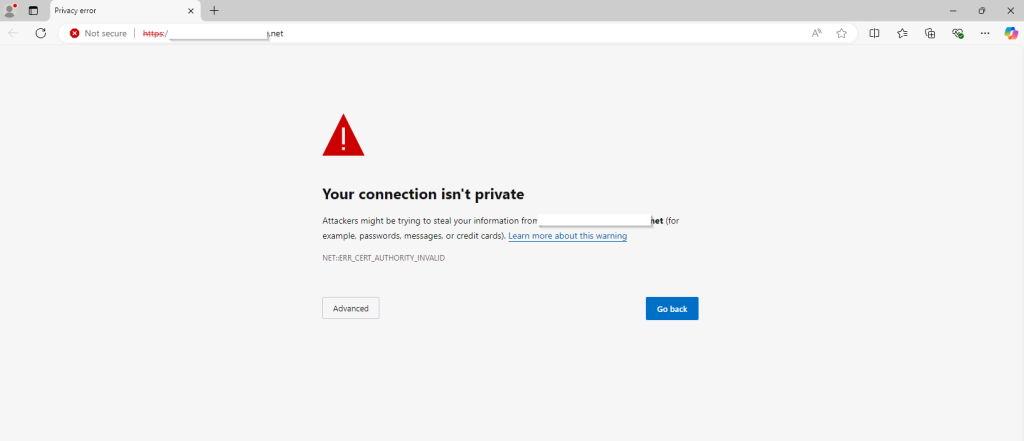
Let’s start from the certificate warning page—the one we want to suppress.
- On the Windows machine, open a web browser and go to the base URL of the vCenter Server using its Fully Qualified Domain Name (FQDN).
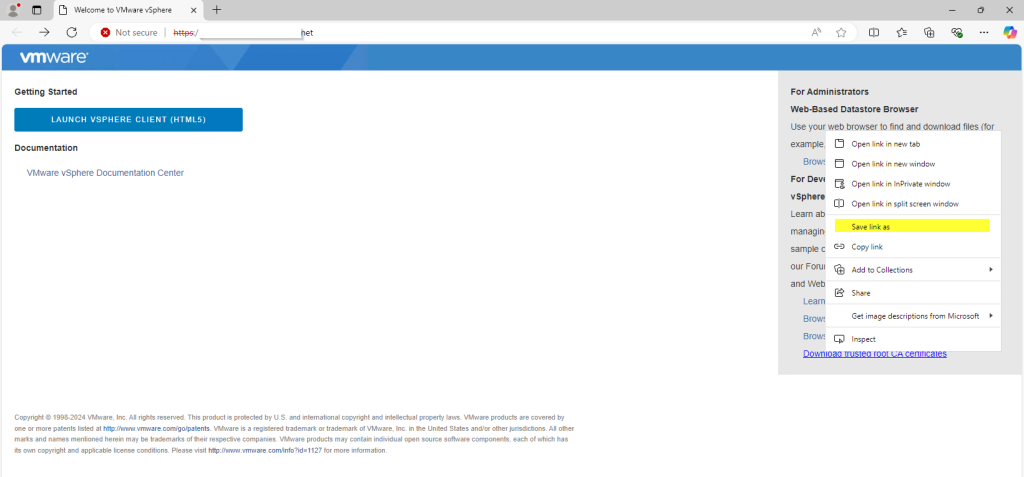
- After you pass the certificate warning, right-click the Download trusted root CA certificates link at the bottom of the grey box on the right and download the file using Save Link as and enter a path to save the file.
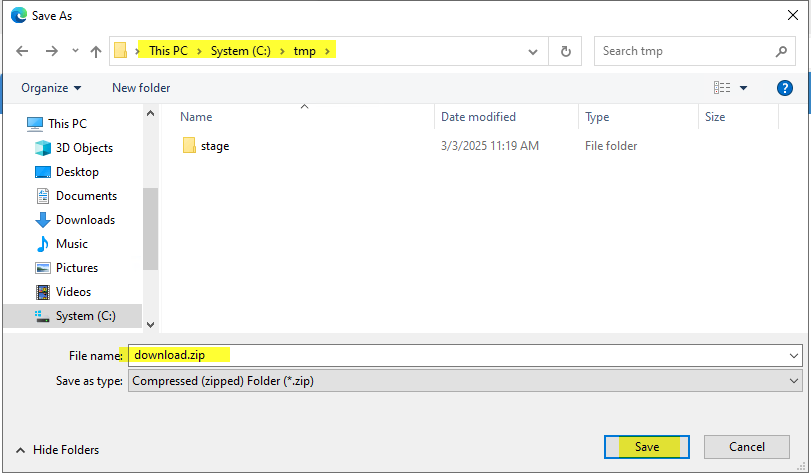
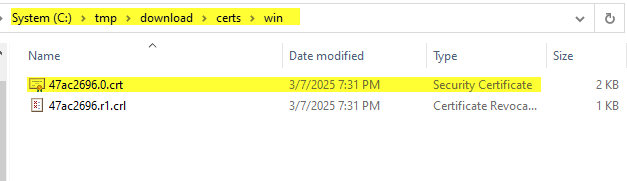
- Downloaded file Download.zip is a ZIP file of all root certificates and all CRLs in the VMware Endpoint Certificate Store (VECS).
- Extract the contents of the ZIP file. The result is a certs folder that contains two types of files.
- Files with a number as the extension (.0, .1, and so on) are root certificates.
- Files with an extension that starts with an r (.r0,. r1, and so on) are CRL files associated with a certificate.
Install the certificate files as trusted certificates on the local Windows machine by following this example:
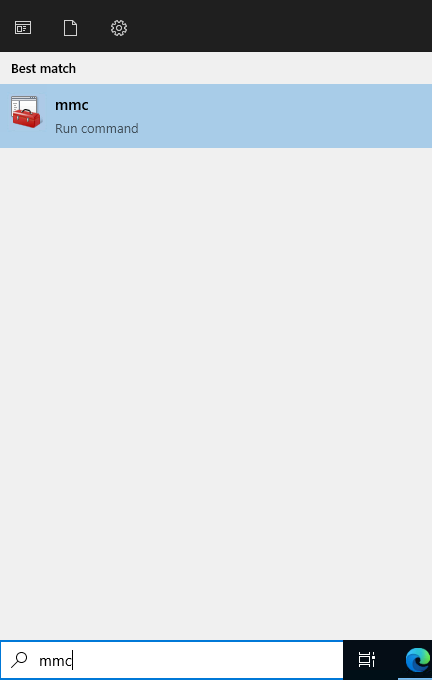
- Click Start, click Start Search, type mmc, and then press ENTER
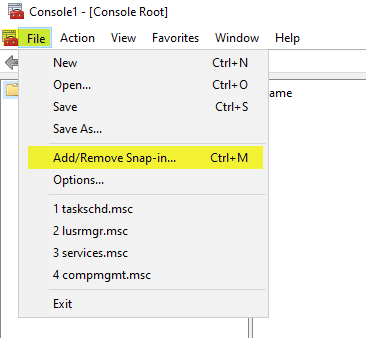
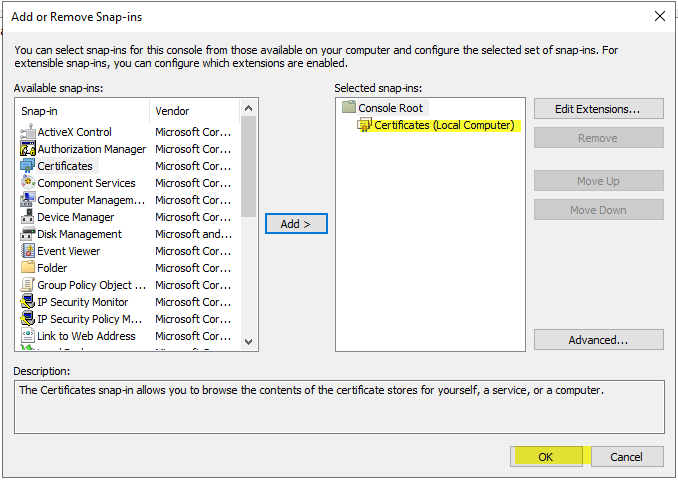
- On the File menu, click Add/Remove Snap-in
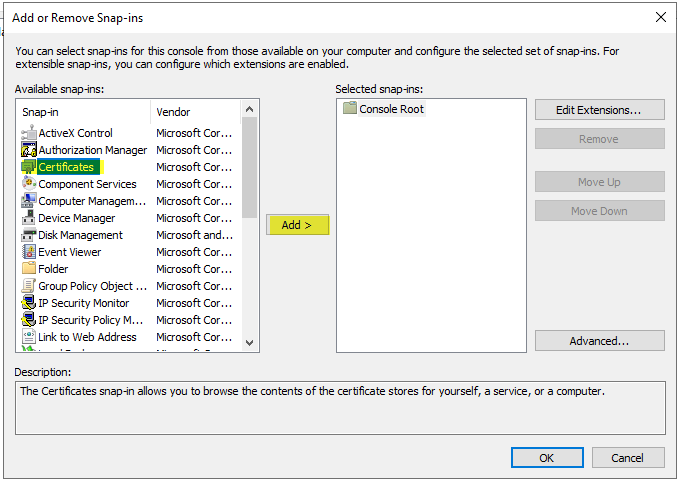
- Select Certificates, and then click Add
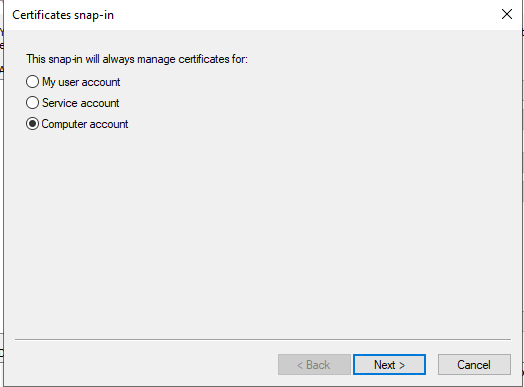
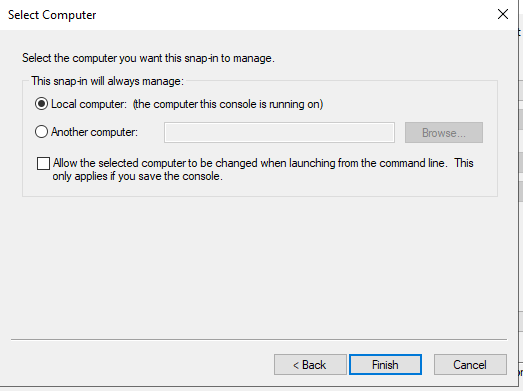
- Select Computer Account -> Click Next -> Select Local Computer -> Click on Finish -> Click OK
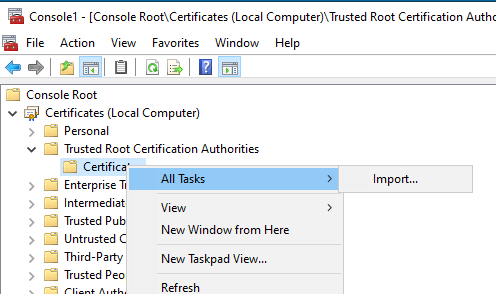
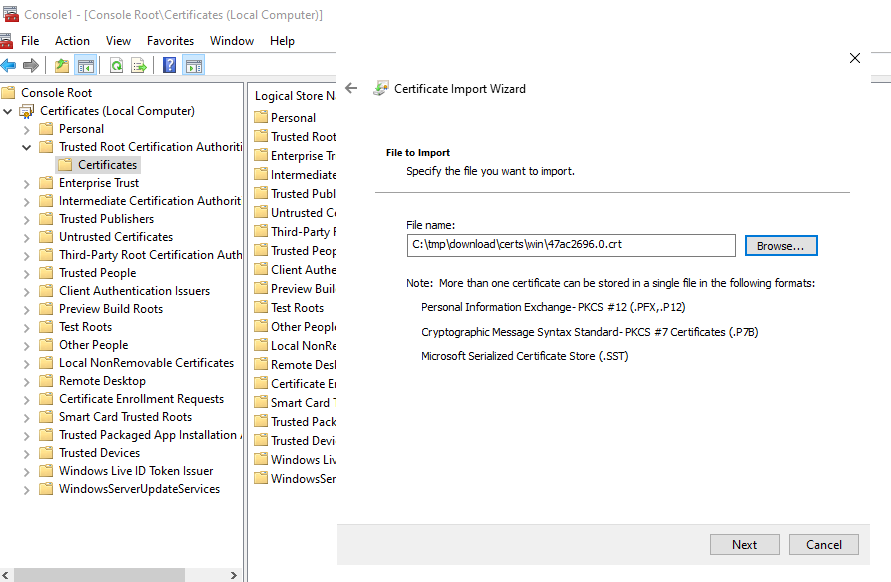
- Select Certificates under Trusted Root Certification Authorities and Right Click -> Select All Tasks -> Click Import
- Click Next
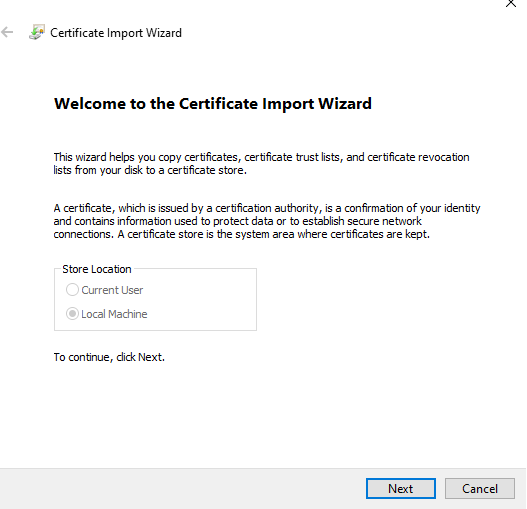
- Enter the path of downloaded Certificate and Click Next
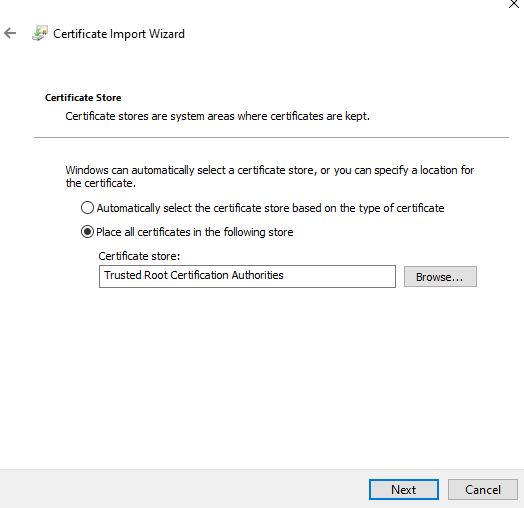
- Select the Certificate Store and Click Next (proceed with the default selection)
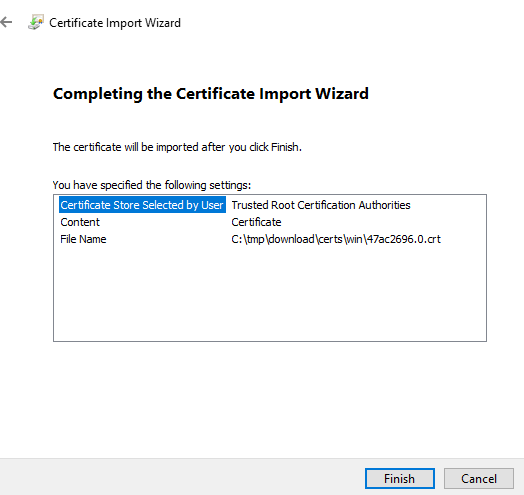
- Verify the details and Click Finish
- If successful, the following message appears. Repeat the same for each Trusted Certificate.
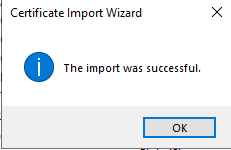
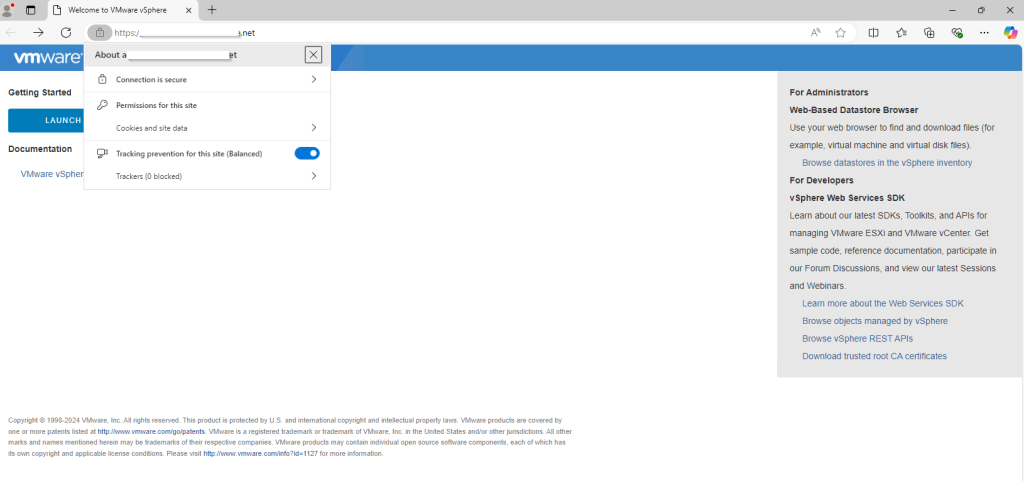
- Close all web browser windows, then reopen the browser and navigate to the vCenter URL.
The error page is gone, and you’ll see a secure padlock icon on the right side of the address bar.
Refer to KB2108294 for alternative methods and a deeper understanding of Active Directory Group Policy updates in deployments using custom certificates or VMCA-signed certificates.