vSphere has a built-in certificate authority (VMCA) that automatically provides and manages the necessary security certificates for vCenter Server and ESXi. This setup works out of the box with minimal effort.
vSphere uses certificates to:
- Encrypt communications between two nodes, such as a vCenter Server and an ESXi host.
- Authenticate vSphere services.
- Perform internal actions such as signing tokens.
Recommended Options for Managing vSphere Certificates
| Mode | Description | Advantages |
|---|---|---|
| VMCA Default Certificates | VMCA provides all the certificates for vCenter Server and ESXi hosts. | Simplest and lowest overhead. VMCA can manage the certificate life cycle for vCenter Server and ESXi hosts. |
| VMCA Default Certificates with External SSL Certificates (Hybrid Mode) | You replace the vCenter Server SSL certificates, and allow VMCA to manage certificates for solution users and ESXi hosts. Optionally, for high-security conscious deployments, you can replace the ESXi host SSL certificates as well. | Simple and secure. VMCA manages internal certificates but you get the benefit of using your corporate-approved SSL certificates, and having those certificates trusted by your browsers. |
In this blog post, we will focus on the Machine SSL certificate from the VECS store.
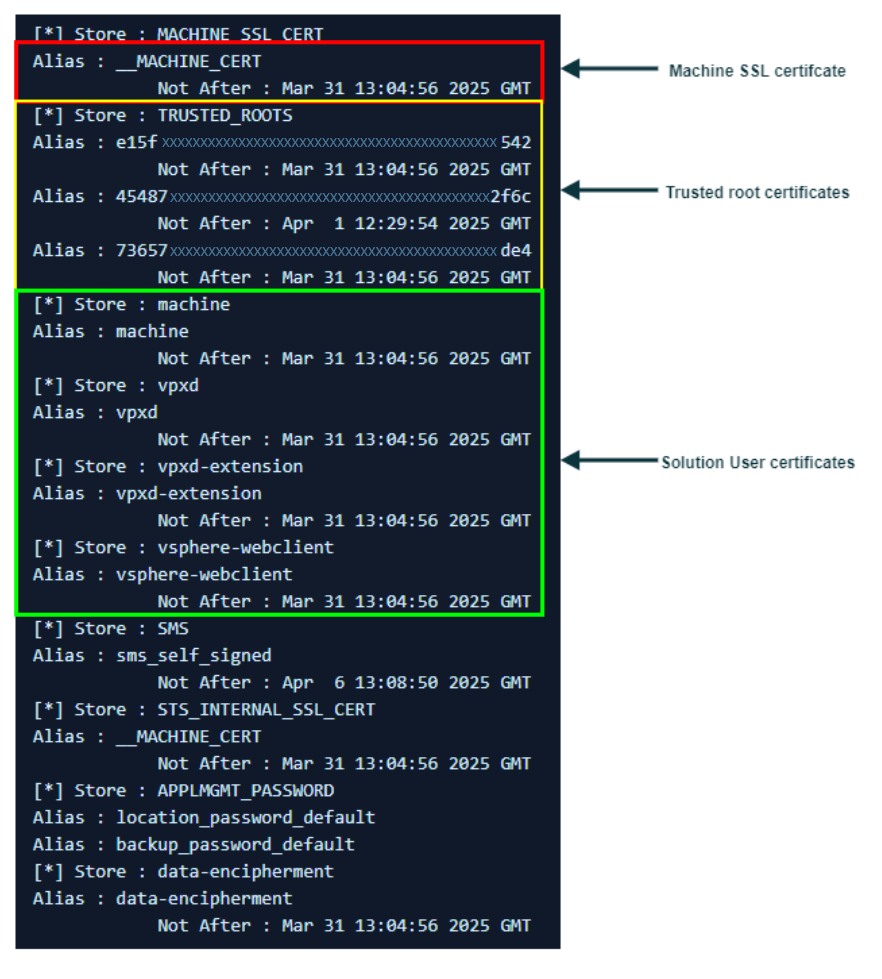
Self-Signed Machine SSL by VMCA
A self-signed certificate is a digital certificate that is issued and signed by the same entity it represents(in our case, the vCenter itself which is called VMCA in the certs context), rather than by a trusted Certificate Authority (CA). Because no external authority verifies it, other systems don’t automatically trust it, and manual configuration is needed to recognize it as valid. These certificates are commonly used in testing or development environment were setting up a CA isn’t required. The term “self-signed” means that the certificate essentially verifies itself using its own public key.
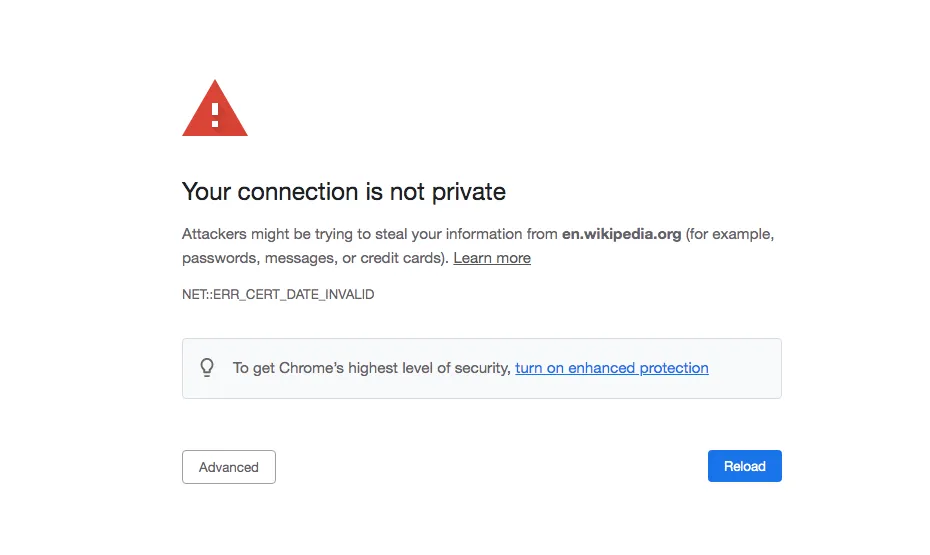
You probably recognize the message from the picture above – this is the step when you manually trust the Machine SSL certificate and recognize it as valid.
*Note* You can download the certificate and import it on the Windows Machine from where you access the vCenter – this way you will not have to validate the certificate every time you access the vCenter Server.
You can find the exact steps in my other blog post.
If you’re not yet convinced about the self signed certificate:
Think about a self-signed certificate like making your own passport at home. You print it, stamp it, and declare it valid yourself. However, airports (other systems) won’t automatically trust it unless they are specifically told to accept it. It might work for personal or internal use (like testing or small environments), but it’s not widely recognized.
Please refer to the following article KB318767 for the exact steps to Regenerate vSphere 6.x, 7.x, and 8.0 certificates using self-signed VMCA.
CA-Signed Machine SSL Certificate by a Third-Party
If your company requires it, you can replace some or all vSphere certificates with ones signed by a third-party or enterprise CA. In this case, VMCA won’t be part of the certificate chain, and you’ll need to manage vCenter certificates yourself in VECS.
You can replace all certificates or take a hybrid approach. For example, you might replace certificates used for network traffic with CA-signed Machine SSL certificates while keeping VMCA-signed solution user certificates. These solution user certificates are only used for internal authentication within vCenter and aren’t involved in external communication.
To continue the passport analogy:
A CA-signed certificate is like getting a passport issued by the government. When you travel, airports and border control instantly recognize and trust it because it’s issued by an official authority. Similarly, when a trusted Certificate Authority (CA) signs your SSL certificate, other systems automatically trust it, making secure communication smoother and more widely accepted.
Please refer to the following article KB316601 for the exact steps to Replace vCenter Machine SSL certificate Custom Certificate Authority Signed Certificate.
Conclusion
Managing vSphere certificates effectively is crucial for securing communication and authentication within your environment. VMCA provides a built-in, automated solution that simplifies certificate management, but depending on your security needs, you may choose to replace some or all certificates with CA-signed alternatives.
For testing and internal environments, self-signed certificates from VMCA are often sufficient, though they require manual trust configuration. However, in production environments where seamless trust and compliance are priorities, CA-signed certificates offer a more widely accepted solution.
For detailed steps on implementing either approach, refer to the VMware KB articles linked above.